The post is a reminder of how TCP protocol establishes and drops/closes a connection. It will be useful when you try to understand a tcpdump/capture in Wireshark.
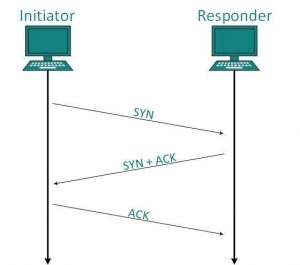
First, everybody knows how a TCP connection starts, right: 3 way-handshake.
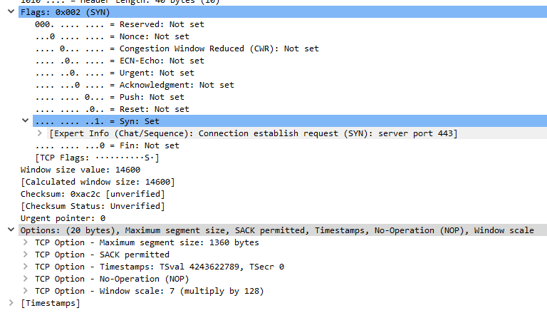
TCP options ( optional extension field ) are announced during the 3-way TCP session establishment. On these options, you can find more on the link at the end of this post.
Typical TCP options in the header are MSS, SACK, Window Scale, and Timestamps.
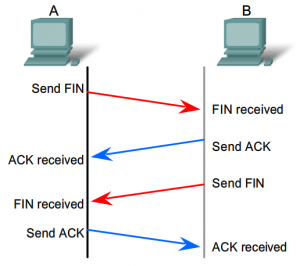
The normal way to close a TCP connection would be using the TCP FIN flag.
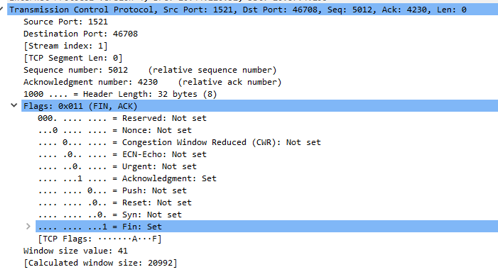
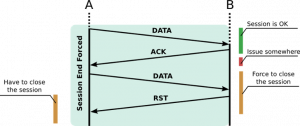
Another way to close a TCP connection is by using the TCP RST flag.
It is used to refuse an incoming connection.
It is used to restart a connection.
The receiver of an RST segment should also consider the possibility that the application protocol client at the other end was abruptly terminated and did not have a chance to process the data that was sent to it.
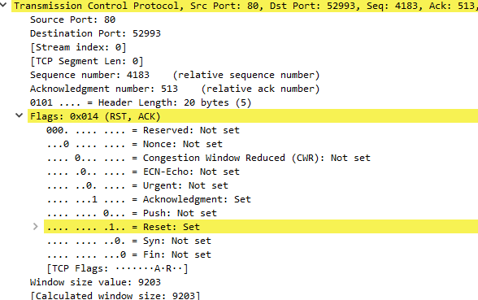
Other important things to know are:
- You issue an SYN if the server replies RST: it means that the port is closed!
- You issue an SYN, if the server does not reply, or replies with an ICMP error: it means that the port is filtered. Likely an IDS / stateful firewall blocking your request.
Useful resource on TCP protocol :
http://en.wikipedia.org/wiki/Transmission_Control_Protocol